Not just websites
Websites that get results
Building superior websites since 2005
- CLICK HERE NOW -REQUEST YOUR FREE QUOTE
Kevin Sample Page Vertical Tabs
What is the difference between policy and procedures?
There are significant differences between policy and procedures
What is the difference between policy and procedures?
Policies are in place many purposes; for cyber security they define your defense posture in the event of an incident.
What is a Policy?
Policy: A policy is a statement that should have clear delineation points that clearly specify its intent. For example, a Policy on Encryption would read “The Board of Directors will ensure that all electronic information that is communicated outside of the business, are encrypted.”
Tip: Many businesses make the mistake of trying to fit in as much as they can into their cyber policy statements. The problem with putting multiple subjects into a policy is that it reduces the effectiveness and makes the policy difficult to understand. It is important to keep policies current and to build the policies into companywide training on a consistent basis.
What is a procedure?
Procedures: Procedures are very specific as to how employees will work, what they will do, and when they will do it. It is important to see the difference between a policy and a procedure; a policy is more of a “here is our rule and why it is our rule” compared to a procedure, which is, “Here is how we will carry out a specific action within our business.” Many times companies will lump together the policy and procedure statements, overall reducing the effectiveness of the actual policy. Procedures change. Policies rarely change.
Policies and Procedures for Cybersecurity:
Standards in cybersecurity are based on industry guidelines. For example these guidelines may be established by the National Institute of Standards & Technology (NIST), the International Organization for Standardization (ISO), or using Control Objectives for Information and Related Technology (COBIT), a framework created by the ISACA (Information Systems Audit and Control Association) for IT governance and management to name only 3.
For example, if a business were to develop a policy noting that all electronic information sent outside of the network environment will be encrypted, they could use NIST guidelines on electronic encryption. A business could search for NIST guidelines and use these to document the guidelines for each department. Best practices could use a blend of the guidelines noted above as each have different approaches regarding best practices. These guidelines generally do not change on a regular basis, but they should be checked on a periodic basis for industry guideline updates.
Tips: The task of developing or updating a policy program for Cybersecurity can be daunting. It may be something that meets resistance. We often hear “our policies have always been fine and we have never been criticized”. Remember, this is not an exercise in futility. The objective is to build a current and relevant policy posture that protects your company.
Resumption Planning
A disaster recovery plan is not the end of it!
What are the differences between a Business Resumption Plan, a Disaster Recovery Plan and an Incident Response Plan?
Many times these critical documents are jumbled together and become ineffective.
A non-technical incident may one where the employees don’t not show up for work. How is your business going to resume operations?
A technical incident may be a hardware failure that effects IT systems or perhaps the email server or internet is down. How will the IT department handle these situations?
These are examples of both technical and non-technical incidents.
A goal of a business resumption plan is to get your business up and running safely and to make sure that the most critical client needs and resources can be met until operations have been restored. A business resumption plan will almost always go hand in hand with the disaster recovery plan. This means that before you can establish a business resumption plan, you must first identify certain aspects of the disaster recover plan to ensure that is possible for the business to be operational before you can begin to recover.
The primary goal of this plan is not to get the business fully operational again, but it establishes procedures to be used during an event. The procedures should be structured to allow the business to get back to a point where the most important tasks can be completed to keep the company afloat. This plan is the step to be enacted after a “disaster” for any company, these the emergency steps a business will use after an event.
Risk assessment
What is our risk, in IT? What technology is critical?
As we discussed in the previous section, policies and procedures are designed to protect the company. When discussing the various threats that impact a business it is easy to focus on the major threats, the most common one’s you might see that have the biggest impact. In reality, Cyber is a vast world with all kinds of different threats. A perfect example of this is the “Cyber Risk Iceberg” (see below). Think of the tip of an iceberg as the “threat”. While we know that the threat is present, we may not be able to see just how much of a threat it really is, like the rest of the iceberg under the water. In this section we will go into each “layer” of the iceberg and assess just what kind of a threat each poses for your company.
Cyber Risk -Iceberg:
Surface Web:
You can see that the surface web of risk can begin with applications that do have inherent risk. Some major websites that seem protected actually have had cybersecurity issues and are not bullet proof, putting you at risk. At this level, we are looking as risks that may include items such as:
Some Different Types…
- Text Hacking (SMS);
- Website Hacking;
- Password Hacking (Interesting Point, the recommended length today is 20 characters!);
- Internal Network and External Hacking; and
- Ethical Hacking (That is what we do!).
So Why Hack?
- Street credentials in the hacking community;
- For Fun & Profit;
- Hacktivist;
- Cyberwarfare between Countries; and
- Publication (Fame) in the recognized and legitimate computer science field.
How about the Deep Web and those risks that we cannot see but know they lurk just under our line of sight?
It is estimated that ninety percent of information on the internet is within the middle of the iceberg. Not accessible from the Tip of the Iceberg!
Some Different Types…
- Corporate Espionage;
- Valuable Data (Financial, Health Care aka HR Dept., Government Records); and
- English is not the only language, gains from multilingual data captures is an increasing target.
So Why Do it?
- Scientific research for Countries to stay abreast of Intel;
- Profit from a subscription of sensitive data; and
- Interruption of Legal Precedence;
Insiders Tip: Trust but Verify! For the safety of your company meet with your Cybersecurity expert to cover your questions and concerns. A second set of eyes with no vested interest could save you from an incident. Protect your reputation, ask questions. More than likely, the cyber professional has worked with situations that are similar to yours and can provide you with assistance to help your company to stay secure.
The Dark Web:
Very rarely do companies delve into this layer of the internet or the risks associated with this part of the iceberg. However, understanding this layer is still critical for any company. This data is hidden. To access it you need browsers and communication services that offer complete anonymity. This is where data can be bought and sold to the open market.
So Why Do it?
- Sabotage;
- Using Encrypted Sites to buy and sell classified information.
- This is the first place we as VTD Cyber look after you declare a breach to see how far the breach has moved on the Iceberg Scale.
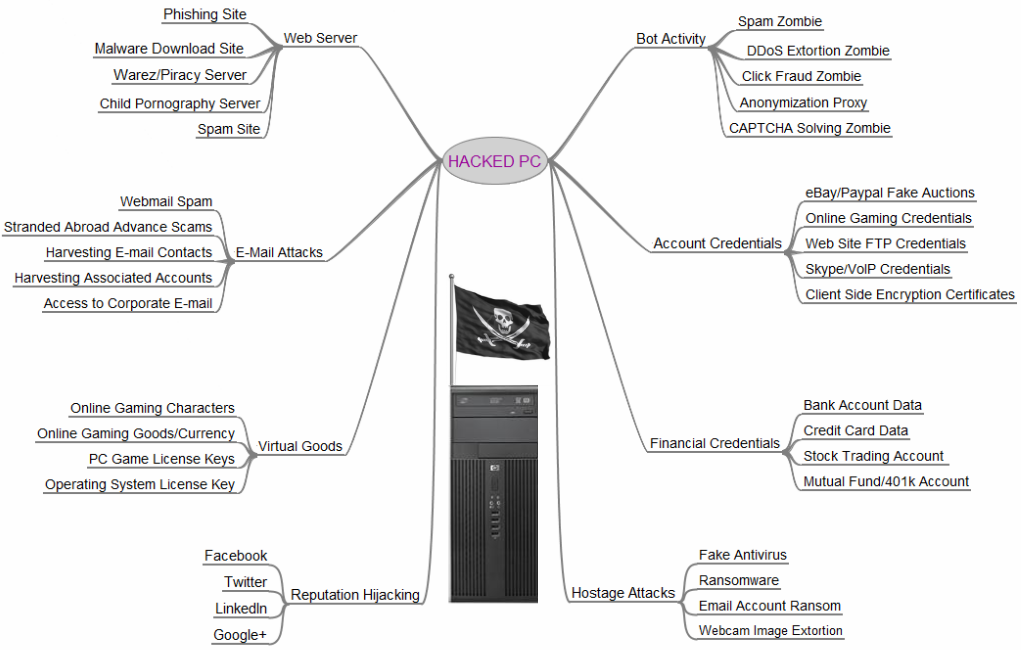
As you can see each layer of the iceberg presents new and increasingly dangerous threats for any business. The example of the iceberg is to show that even the most common place things, like a simple website on the internet, can actually host a long list of risks to the security of any company/individual. This does not only apply to websites, but also even to services such as email. In the graphic below is a chart that assesses many of the ways in which emails can be hacked and used against an individual.
Anatomy of the Value of Data: “Your Email Account May be More Valuable Than you think! Take a Look”
**This following chart is provided from Krebs, a Security Researcher.
If we look as the various values of an email we can see the 6 value points for one email:
- Privacy: This risk can be used for a ransom situation. Pay or risk going public with the information.
- Retail resale: Today, it is common to buy a stolen account that can be used for things like downloading music or movies. The gain here is simple, download items of value that cannot be traced. Most cyber fraudsters will not steal physical assets, if you purchase a large TV or furniture, there is a delivery address. So, most fraudsters will download software load it onto a server and sell the software package.
- Financial: capture an email in transit or even as it sits in an account, there may be a number of financial data records that contain value. The primary use for this information is heist, manipulation of the account holder or opening a line of credit. Again, email can contain a number of items of value that can be manipulated and sold for their value on the Deep Web.
- SPAM: Why SPAM? What is its purpose? SPAM has morphed in its value. Today, Facebook and Amazon to name a few examples use SPAM to target social media accounts that you use. It is targeted marketing. In the past, SPAM was infected with bad intentions. However, as SPAM has grown in value to clients like Facebook, Yahoo, Microsoft and Amazon – SPAM is no longer used as it once was. It still is used as an infection point but there may be more value in selling SPAM to high paying customers that are in the social media industry.
- Harvesting: This category is a general overlay of all items we just spoke about. After millions of emails are obtained, they are harvested for key words such as: bank, login, commodity prices such as gas or milk (which would be purchased by a social-media firm to target grocery store pricing on said commodity). This leads us into the introduction of smart devices in our homes and businesses. Nothing comes free. These devices like Google, Alexa and Apple listen and key words are probably entered into a database, for parsing later, as projects arise.
- Employment: Hiring employees and dealing with their employee benefit plans and other sensitive information can be divulged from a hijacked email. We often will see that the CV is attached in clear text, as is the application and copies of transcripts, investments like 401K accounts are often sent to the new employer. After interception, this data is now parsed out and sold within the Dark Web.
This is all of the information that can be taken even from just one email, let alone the thousands of hacks that occur on a daily basis. The more we dive into the threats that arise from the use of the internet the more it becomes apparent that protection and caution is vital in order to keep your business safe and operating.
Offensive-Security
How can we defend?
Now that we have reviewed many of the threats that arise from the internet we will cover some of the ways in which you can protect yourself from these risks.
What is the best way to stay protected?
In today’s world, the easiest way to stay protected is to have an offensive approach to security. Do everything in your power to prevent an attack. With an offensive approach you stay ahead of the threats that are coming your way, increasing the odds that you won’t have to deal with the messy clean up that comes after an attack.
In today’s companies the IT Department is the defensive team. The CIO or IT Director is also on the defensive team.
Offensive vs Defensive postures.
Reducing risk from a defensive posture is focused on traditional controls. Defensive controls include the thought process that:
- a firewall is installed
- an intrusion prevention program is in place
- policies are in place
- we have an IT Professional that devotes ten percent of their time within the security realm
- Our IT team updates the firewall requires and updates our security software or change.
- They periodically review and update our security policies and rules
- They are responsible for patch security releases within your company.
An offensive posture is polar opposite. Due to the ideas of traditional management and IT relationships, the offensive concept can be difficult to introduce into your culture.
In progressive companies:
A Chief Information Security Officer (CISO) is hired. The CISO doesn’t report to the CIO, rather they report to the Audit Committee or designated Committee. The primary reason is simple. The two IT roles are diametrically opposed to business goals and how technology is deployed and managed. If a CISO falls under the CIO, they are subordinate. Hence, CISO goals can be over ruled. This is very common and increases friction and maybe animosity within the “camps.” A progressive CISO that reports to the designated Committee will improve the offensive security posture by offering fulltime and devoted resources to technology projects, current security labeled devices such as firewall and intrusion prevention controls.
Assignment of responsibility to monitor security notifications:
Monitoring software produces an overwhelming number of logs that come into a typical business that must be evaluated and reacted upon, 24×7. Time devoted to being offensive is spent in correlating attacks on your business, which can take months of investigation and correlation and making changes to the technical environment that may not be popular. They may make decisions that reduce availability to resources as dictated by the threats that have been identified. The primary mission statement for a CISO is simple: CIA which stand for the Confidentiality of data, Integrity of data and Availability of data. Associability of data is also an important goal.
When considering the introduction of an offensive security posture you will want to fully explain the shift. There will be friction. Change can be difficult. The shift can also threaten existing technical staff as they may feel they are giving up some authority. Encourage team-work and empower the CIO and CISO to work together but respect the main concerns that arise throughout the day, week or year.
Request Your Free Quote
We would love to hear from you.Simply fill out the form below and we will be in touch shortly.
Offices
7650 Dean Martin Drive, #101
Las Vegas, NV 89139
104 East State Street, Suite J
Redlands, CA 92373
Contact
Office (702) 659-9901
Office (909) 793-3456
Social
© COPYRIGHT 2025 BenchMark Website Design FIND US